The hack is the largest cryptocurrency heist in history. Bybit is currently actively working with industry experts such as Chainalysis to trace the stolen assets and is investigating the theft.
The company also launched a recovery compensation program to compensate individuals who help recover assets with up to 10% of the amount recovered. Chainalysis has explained how the vulnerability occurred and what the attackers used to
The company announced how the tactics, techniques, and procedures (TTPs) used by the cryptocurrency miners are linked to North Korea, and that Chainalysis is working with Bybit and law enforcement to help recover the funds.
The Bybit hack illustrates the evolving tactics used by nation-state cybercriminals. In particular, it is unclear what methods North Korean-linked hackers are using to
Recently, according to the 2025 Virtual Asset Crime Report published by Chainalysis, North Korean-affiliated hackers will be responsible for approximately 20 hacks in 2023.
In 2020, $660.5 million (approximately 98.8 billion yen) was stolen, and in 2024, $1.34 billion (approximately 200.4 billion yen) was stolen in 47 hacks, more than doubling the amount stolen in one year (1
The Bybit hacking incident is estimated to have increased by approximately $160 million (approximately 2.02%) from the total amount stolen by North Korean hackers in the entire year of 2024 in a single hack.
The attack is a good example of a hacking technique often used by North Korea. Hackers use social engineering attacks to get close to their targets and then use complex
They are using money laundering techniques to hide the stolen funds. In fact, the funds stolen in this Bybit incident were added to the same addresses as assets seized in other North Korea-related hacks.
This further proves that this incident was a nation-state-sponsored act. Below is a step-by-step analysis of how the Bybit hacking incident took place.
1. Initial intrusion via social engineering techniques Hackers used phishing attacks to trick cold wallet signers.
The attackers broke into the blockchain and tricked users into signing transactions that changed a secure multi-signature wallet contract into a malicious one.
During a routine transfer of Ethereum from Bybit’s cold wallet to its hot wallet, the attackers stole 401,000 Ethereum tokens, worth approximately $1.5 billion at the time.
The stolen assets were transferred via a complex network of intermediary addresses, which
It is a common technique to conceal the path of funds and make it difficult for blockchain analysts to trace them.
The hackers exchanged most of the stolen ETH for other tokens such as BTC (Bitcoin), DAI (Daicoin), and distributed cryptocurrencies through decentralized exchanges (DEEXs).
X), cross-chain bridges, and instant swap services with no KYC procedures were used to move assets across multiple networks.
5. Funds Idling Stop and Strategic Money Laundering Most of the stolen funds were left in multiple addresses. This is
A common strategy used by North Korea-linked hackers is to avoid being tracked after a high-risk incident by leaving funds idle until scrutiny eases, rather than immediately laundering money.
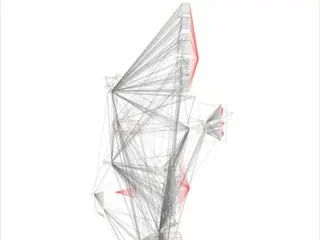
The Chainalysis Reactor graph shows the complex chain of events that led to money laundering. The graph shows the intermediary addresses, token exchanges,
It also illustrates the attempt to conceal the stolen funds through a complex network of cross-chain transfers, and the ripple effects this incident will have across the crypto-asset ecosystem.
Despite the severity of the Bybit attack, the inherent transparency of the blockchain poses a significant barrier to malicious actors attempting to launder stolen funds.
All transactions are recorded on a public ledger, allowing authorities and cybersecurity companies to track and monitor illegal activities in real time.
Chainalysis also recently acquired Hexagate and Alteriya to further strengthen its security and fraud detection capabilities, providing more advanced
Cooperation across the crypto asset ecosystem is essential to addressing the threat. Bybit’s promise to compensate customers for their losses and Blockchain
Our close collaboration with forensic experts demonstrates the importance the industry places on mutual support and resilience. With all our experts coming together, the crypto community can achieve a high level of service.
Chainalytics is a global leader in financial services, with a team of globally located, customers and partners in the public and private sectors.
We are working with our partners to support various asset seizure and recovery routes in response to this attack. We have already worked with multiple parties to recover the 4,000 stolen from Bybit.
The company has contributed to freezing over $57 billion (approximately 57 billion won) in funds and will continue to work with public and private sector institutions to seize as many assets as possible.
2025/02/25 16:49 KST
Copyright(C) BlockchainToday wowkorea.jp 117